| Deep Web vs Dark Web: What’s the Difference? | 您所在的位置:网站首页 › difference between Esport › Deep Web vs Dark Web: What’s the Difference? |
Deep Web vs Dark Web: What’s the Difference?
|
The main difference between the deep web and the dark web is that the deep web is bigger and used every day by most people without even realizing it. The dark web can only be accessed with the Tor browser and is riskier to access than the deep web. Continue reading to learn more about the differences between the deep and dark web, and how you can keep your information protected from both. What Is the Deep Web?The deep web, also known as the hidden web, is the part of the internet where almost all online activity happens. The deep web consists of sites and databases that are not fully accessible to standard search engines such as Google, Bing and Yahoo. This could be because the pages are not indexed, meaning they can’t be found by searching for them on search engines, they are paywalled websites or private databases. In order to access deep web content, you’ll need the direct link or sign-in credentials that grant you access to it. Some examples of things you’d find on the deep web include the following: Medical records Membership websites Fee-based content Paywalled publications Academic journals Deep web use cases Paid Subscriptions: The deep web is used to access all types of paid subscriptions such as streaming services like Netflix and Hulu. Accessing Accounts: One of the main uses of the deep web is to log in to accounts such as social media or bank accounts. Online Payments: Whenever you go to pay for something online, you enter your payment information through the deep web. What’s the Dark Web?The dark web is a part of the internet that provides anonymous and secure communication channels that can only be accessed with a special browser called Tor. Average users of the internet will not stumble upon the dark web. Going on the dark web has to be intentional since it requires a user to have specific tools to access it, such as the Tor browser and a VPN. Here are some of the things you can find on the dark web: Illegal and stolen data (e.g. stolen passwords, credit card numbers, social security numbers) Drug trafficking websites Chat forums Forged data (e.g. fake passports) Whistleblowing websites Dark web use cases Anonymity: Many people use the dark web because they want to remain anonymous. For example, citizens who are a part of oppressive regimes use the dark web to speak freely. Selling Personal Data: Cybercriminals often use the dark web to sell stolen information that has been leaked in data breaches. For example, they may sell account login information, credit card numbers and Social Security numbers, to name a few. Illegal Purchasing: People use the dark web as a way to purchase things that they can’t get anywhere else because they’re illegal. This includes drugs, weapons and stolen data. Deep Web vs Dark Web: Which is Bigger?The deep web is the largest part of the internet. According to Dataprot, a rough estimate is that the surface web makes up only 5% of the internet and the rest is made up of the deep web. The surface web is anything on the internet that you’re able to search for on standard search engines. According to SpiceWorks, the deep web hosts around 7,500 terabytes of data, whereas the surface web hosts 19 terabytes. It’s also estimated that there are 550 billion individual documents that are hosted on the deep web and only one billion are hosted on the surface web. The dark web is considered to be a smaller subset of the deep web. According to Britannica, the dark web makes up only 0.01% of the deep web. 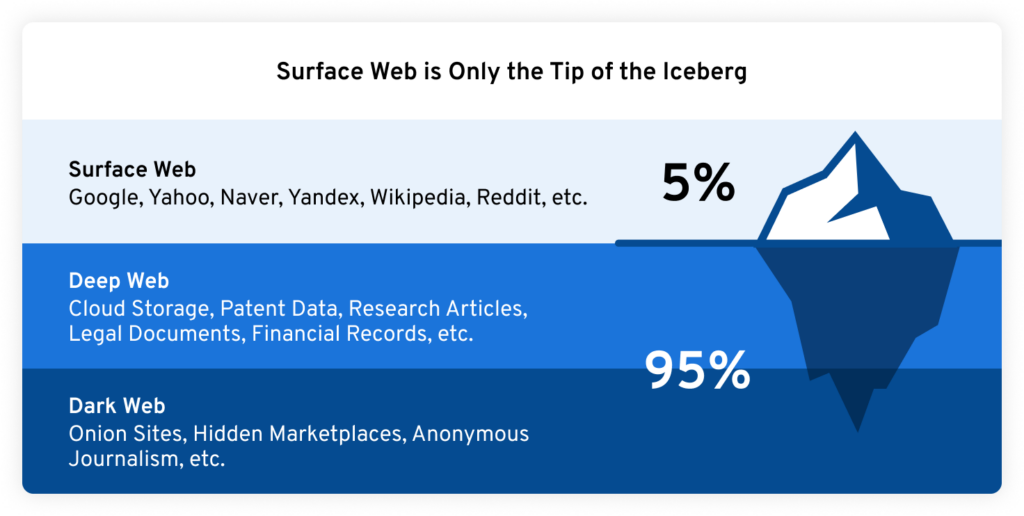 Deep Web vs Dark Web: Which is Riskier to Access? Deep Web vs Dark Web: Which is Riskier to Access? Both the deep web and dark web come with their risks, however, the dark web presents a greater one. Because the dark web is home to all kinds of illegal activity, clicking on the wrong thing can place your device at risk of becoming infected with malware or other viruses. Malware is a type of malicious software that can spy on you, log your keystrokes and steal your personal information. The information and data cybercriminals are able to access depend on the type of malware installed on your device. How to Keep Your Information Safe on the Deep and Dark WebHere’s how you can keep your information safe on both the deep and dark web. Use strong, unique passwordsOne of the best ways you can keep yourself and your information protected is by using strong, unique passwords for each of your accounts. Strong passwords are at least 12 characters long and contain upper and lower case letters, numbers and symbols. To make your accounts as secure as they can be, make sure you’re not reusing or using variations of the same password across multiple accounts. Coming up with strong passwords and memorizing them all is next to impossible to do on your own. We recommend using a password manager to aid you in generating, managing and securely storing all your passwords, passkeys and data. With a password manager, the only password you’ll have to remember is your master password. Enable MFA on your accountsMulti-Factor Authentication (MFA) is an extra layer of security you can enable on your accounts. MFA protects you in the event that someone is able to gain access to your login credentials since it requires a second method of authentication before they’re able to successfully log in. Subscribe to a dark web monitoring serviceDark web monitoring is when a tool is used to scan the dark web for your personal information such as your email address or credentials. This can be done manually with a free service that doesn’t notify you, or it can be done automatically with a tool that detects and notifies you when your credentials are being sold on the dark web. A dark web monitoring tool that is constantly scanning the dark web for your personal information is the best option for keeping you and your data safe because you’ll receive dark web alerts and can take action immediately if your credentials or information are compromised. Scan Your EmailOne dark web monitoring tool that works alongside Keeper Password Manager is BreachWatch®. BreachWatch monitors for suspicious activity on the dark web and alerts you as soon as any dark web activity matches the credentials stored in your Keeper Vault. When one of your records shows as “high-risk,” you’ll receive a notification and Keeper will help you change your password to one that is strong and unique. Maintain good cyber hygieneCyber hygiene refers to cybersecurity best practices that everyone who actively uses the internet should be implementing to keep themselves and their data protected from common cyberthreats. Some cybersecurity best practices you should follow include: Using a personal firewall Using a Virtual Private Network (VPN) Having antivirus software installed on your computer Regularly updating your software, apps and devices Regularly backing up your data Checking if links are safe before clicking on them Being cautious of unsolicited attachments Not responding to requests for personal information Stay up to date with the latest cybersecurity newsTo know about the latest cyberthreats people are falling victim to online, you should keep up with the latest cybersecurity news. This will help you know what type of attacks to be on the lookout for when you’re browsing online. Stay Safe on the Deep Web and Dark WebBeing an active internet user means there’s always a possibility that your information is vulnerable to being stolen, which is why it’s important you take the necessary precautions to keep yourself and your data protected. While we don’t recommend you access the dark web, if you do decide to, make sure you take all the steps above to keep your data safe from cybercriminals. The same steps apply when using the deep web. Start a free 30-day trial of Keeper Password Manager today to begin securing your accounts from common cyberthreats on all parts of the internet. |
【本文地址】